There is a certain scheme of crypto scam I have come across which is not a usual ‘bitcoin investment’ enticing you to put your money into some ‘binary trading’ establishment in a hope for sky high profits. This is a cloud mining offer which eventually does not seem like a straightforward scam for some, however it is still dangerous if you are not aware of some important details and general principles of securing your crypto wallet.
Mining wallet
This is a perfectly normal Instagram guy, neither a financial consultant nor a wealthy trader promising 1000% ROI.
What he offers is a bitcoin mining service using blockchain.com platform. Of course, it is secure as hell. At the end, why not accumulate some crypto just by mining it.
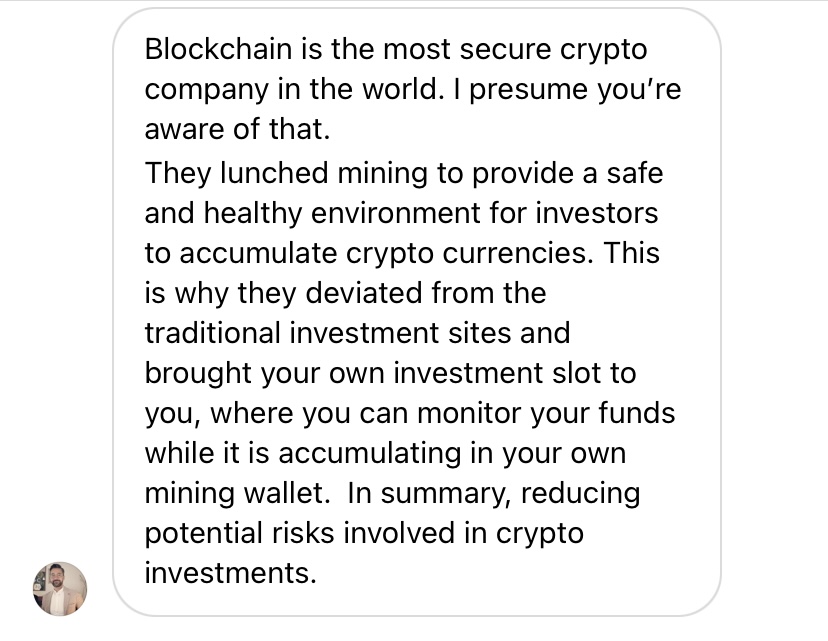
Technical aspect of the mining process is pretty simple: you create a ‘mining wallet’ on blockchain.com which is then ‘synchronized’ to a ‘mining server’. As simple as that: you start then to accumulate bitcoins in your wallet. Why you need this mining wallet? A very simple explanation follows:
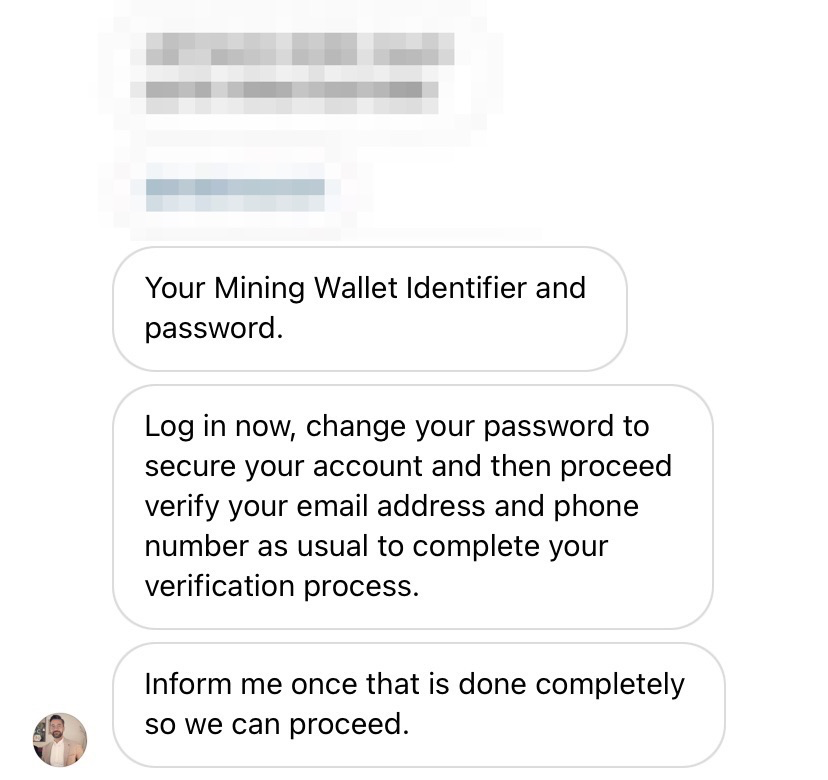
And for my convenience, he even creates a wallet on blockchain.com for me and sends me its ID and password! Of course, security is the key concern, so he prompts to immediately change the provided wallet password before mining starts. Seems safe!
Indeed, the technical mining capabilities are pretty impressive:

One last thing is needed actually to initiate the process, and it is a one-time deposit to your mining wallet. The deposit is only $3,000 and you don’t even need to spend it or send to anyone. It stays in your mining wallet and can even be withdrawn when needed. Now, how cool is that?!
And it is all safe and sound, because it is your wallet and you (hopefully!) just changed its password.
The catch
Those who are keen on crypto wallets security, may have already spotted the simple catch.
In this scheme, the scammer:
- does not provide any scam website to register on;
- does not ask to deposit money to any external address except your own wallet;
- prompts that you change the wallet password, thus creating a false feeling of security.
What is behind the scheme, however, is the fact that anyone having blockchain.com wallet password can easily get an access to a recovery phrase in the wallet which, in turn, would give an access to the funds – the funds a victim is prompted to deposit into ‘his’ wallet. And this is exactly how a scammer gains an access to the wallet and the deposit in it later on. T
To put it very simply, owning the recovery phrase means owning your wallet private key. How often do you grant your apartment and car keys to a complete stranger you don’t know?
Getting a recovery phrase in blockchain.com wallet is fairly simple using ‘Security’ menu (well, as in many other crypto wallets out there as well):
Why this scheme might easily work on a gullible user who is not aware?
They are explicitly prompted by a scammer to change their password afterwards, and this gives a false feeling of security. Indeed, what can happen if you change a password, add and confirm a phone number and activate 2-factor authentication in a newly created wallet? Well, possessing a recovery phrase gives an immediate access to a wallet and funds in it, this is what happens:

Just a couple of links to blockchain.com support section explaining how recovery phrase and private key works:
- https://support.blockchain.com/hc/en-us/articles/360000951966-Public-and-private-keys
- https://support.blockchain.com/hc/en-us/articles/115001298143-Your-Secret-Private-Key-Recovery-Phrase-The-Failsafe
Such a scheme is also a reason some of crypto wallet providers are temporarily disabling an access to recovery phrase for the users in order to prevent them from sharing it easily with scammers, like for example SwissBorg mobile app did recently:

Following the money
Is there any way to investigate the money flow if we don’t even have any wallet address from the scammer? The answer is no, unless a sucker punch is used. Which I actually used this time in order to scam the scammer back, sorry buddy:

Don’t expect this sucker punch to work every time, to be honest. But this scammer has generously sent me a $3 transfer in BTC, as per my kind request. This allowed to have a look at some money flows in the proximity of the wallet he used. And oh yes, I have captured his IP address as well.
In our case, the wallet which scammer used to send me that nice little $3 bonus, traces to Binance exchange, so much favoured by many scammers out there:
There are two branches here both leading to Binance, the first through scammer’s wallet (middle) and the second the other way (left).
Same flow visualized using GraphSense tool, this one gives a more clear representation of transferred sums in USD. By checking intermediate wallets balances we can make sure that the deposit to a scammer’s wallet has reached Binance exchange, even it has been mixed with other funds in the course transactions with multiple inputs and outputs:
By checking intermediate wallets balances we can also make sure that the initial deposit to a scammer’s wallet has reached Binance exchange at some point, even it has been mixed with other funds in the course of intermediate transactions with multiple inputs and outputs:
Lessons to be learned
Remember that one should never use a bitcoin wallet created by someone else, or if someone else had even a temporary access to it.
Remember that changing the wallet password, or even securing it with 2-factor authentication will not help if someone already knows your private key or a recovery phrase.
Learn the importance of properly securing your private key. It is a key to your money.








