Definitely many of us have heard of sextortion, an online scam scheme already existing for at least a few years which usually targets victims of breached passwords. A monetary part of the scam consists of a claim to send bitcoin ransom in exchange for not sharing publicly some private photos or videos of you, which scammers claim they own (hint: they don’t).
Bitcoin sextortion scams […] email you to say they’ve videoed you on your webcam performing sexual acts in private, and ask you to pay them amount in Bitcoin to keep the video (which doesn’t exist) private. This type of blackmail has become quite popular since the middle of 2018.
blog.malwarebytes.com
They know your password (at least one)
The tricky part here is that scammers actually present a victim with their actual password which is associated with victim’s email and has been leaked from a certain website which has been exposed to a data breach. The databases of such leaked credentials are actually quite easy to obtain on dark web markets or might even be available on the open web as well.
So, one day you may get this:
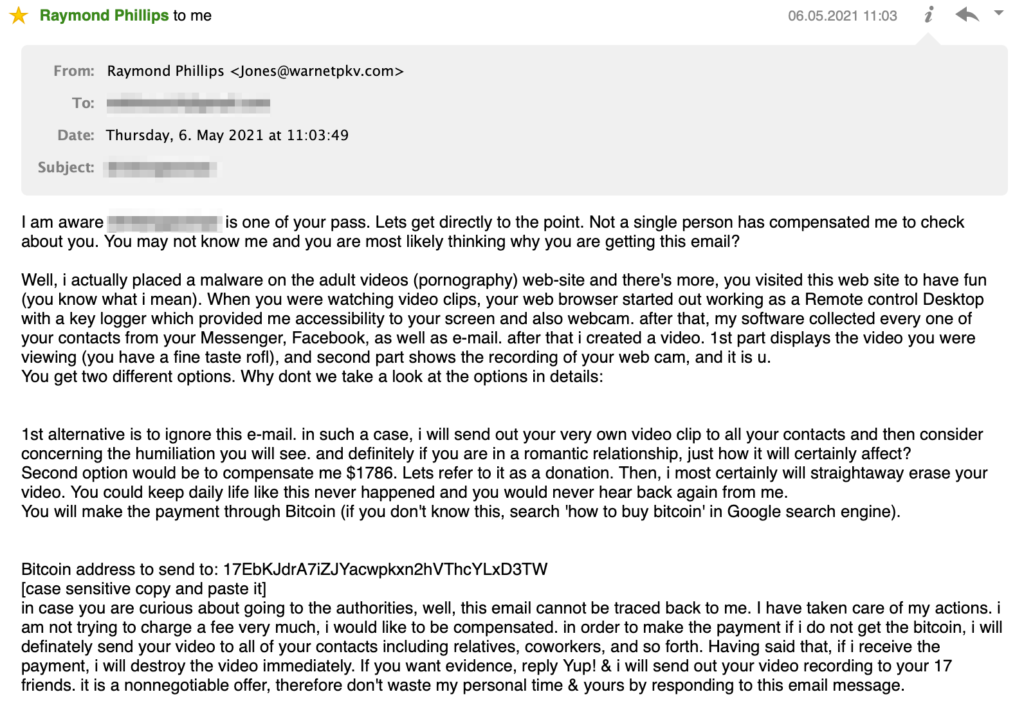
This email contains a real password which I have used at least on a few sites before, and it is not really possible to understand which site exactly has leaked it. Anyway, seeing your actual password in a email from stranger already would bring some anxiety to anyone.
Yet another scam email variety, as described in the above mentioned article from MalwareBytes, includes spoofing a sender’s email FROM address so it looks like the email was sent from victim’s address (though it is well known that FROM field in a email is a plain text string which can hold virtually anything, still, a not so technically keen user might be easily mislead by this). It also contains a bitcoin address which is split into two substrings supposedly to get through certain email spam filters:

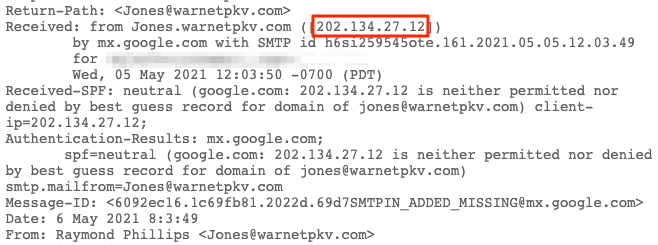
Scam email origin
The email message originates from IP address 202.134.27.12, which is a dynamic IP address from a pool of Tonga Communications Corporation (yeah that’s pretty far!). Obviously this IP doesn’t reveal an actual scammer’s location and most likely it was acting as an open mail relay when the email was sent through it (at the moment of article writing this IP address doesn’t appear to be online):
I might guess that such emails might be actually originating from anywhere in the world, as it should be pretty easy to find an open mail relay to send unsolicited emails.
Bitcoin addresses investigation
The email I have received to my personal mailbox contains BTC address 17EbKJdrA7iZJYacwpkxn2hVThcYLxD3TW, but unfortunately (for us, but not for the scammer) this is a newly created address having no transactions, so it can’t be investigated. But turning once again to scam email example from MalwareBytes article, we have at our disposal address 1C1FfgyNsJGJZfuR2ePXxTraaCqE6WLWSM with 2 transactions, so we can investigate sextortion related money flow using this address as an example.
Note the original email timestamp which is 31.12.2020 01.32 (nice New Year gift from a scammer, isn’t it?). The input transaction d60cffa4c95abe7768fcf9f8a784c7aa29a942b066e039b1430ed6694f608c53 involving scammer’s address then recorded in blockchain at 01.01.2021 19:48. This transaction has total of 11 inputs summing up to 0.03579 BTC, which is equal to 1,052 USD at the time of transaction. So this is really close to a requested ransom amount of 1000 USD.
Next, the output transaction 6ee6fcc88361f428d26d2cf396fb6e560bad71326df9f81dc4b829fe80c582b0 happens only 3,5 hours later at 01.01.2021 23:31 and is done by a scammer to move money.
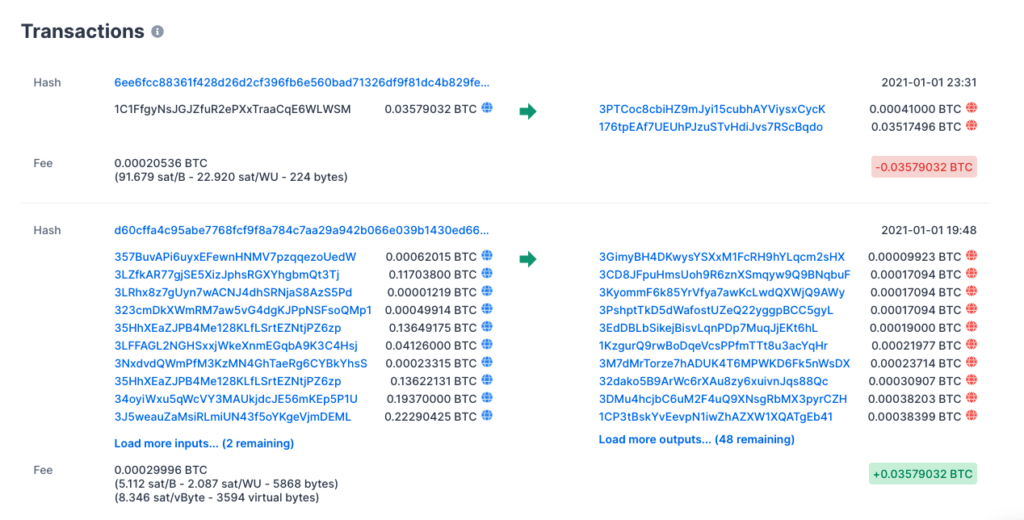
Putting all these factors together, we may be pretty much sure that this transactions around 1C1FfgyNsJGJZfuR2ePXxTraaCqE6WLWSM address actually involve a scam victim paying 1000 USD ransom and then a scammer moving money further.
Following the money
We are using GraphSense tool to track and visualize money flow for this particular case. Our objective here is to understand the destination of funds which were initially sent to scammer’s address, thus revealing possible points of cashing out.
Bitcoin addresses clustering
GraphSense utilizes clusters in its visualizations, whereas a cluster is basically a group containing one or more bitcoin addresses which are logically connected based on their computed similarity: activity, relation to the same entity like a crypto exchange or other different properties.
Most simple case is a cluster of one address, when we don’t know anything about its relations with any other address. On the contrary, there are clusters belonging to very big entities like exchanges, which might contain thousands or even millions of addresses.
The simplest example logic for clustering might be based on detecting addresses spending funds together. This said, addresses are attributed to the same cluster, if they are co-spent in one transaction. So if addresses A and B are co-spent in transaction T1, and addresses B and C are co-spent in transaction T2, all addresses A, B and C will be part of one cluster. In reality, many more different heuristics can be used to determine clusters of addresses.
Below is a money flow diagram which depicts transactions and entities around scammer’s address. Funds are coming from some really big cluster of addresses in 11 inputs, and then moved out within two logical branches using a few intermediary addresses in different clusters:
Upper branch leads us to CoinPayments.net payment gateway / crypto wallet service, whereas the lower one is related to RenBTC.
RenBTC is one pretty interesting project in crypto world, which represents a unique token whose value is anchored to the value of Bitcoin. This said, 1 RenBTC is equivalent by definition to 1 BTC, although the first is actually a ERC-20 token running on Ethereum. To put it very simple, it provides a way to seamlessly move funds between Bitcoin and Ethereum blockchains. More detailed general description can be found in this article, and some technical details are here. Obviously, funds moved between different blockchains are harder to track and in our case it could be a subject for a separate in-depth investigation.
Basically, CoinPayments.net would be one of the possible points to cash out the funds in this case.
Some closing remarks
To put it very short, scammers will continue to exploit any imaginable human weakness to steal bitcoins as long as people fall into weakness and use bitcoin.
Hopefully the reader has enough common sense to never be lured into sextortion email scams and lose money this way. Check an article by Nadia Aimé for simple yet effective advices how to avoid being a sextortion scam victim.
I also highly recommend taking a look at an article by Jaeson Schultz, which presents a whole collection of such sextortion scam emails varieties. Written in 2018, it is still very relevant today.
